
Critical Vulnerabilities in Webmin & Apache Parquet- Mitigation
Explore critical vulnerabilities in Webmin and Apache Parquet and learn effective mitigation strategies for enhanced cybersecurity.
5/5/2025

Explore critical vulnerabilities in Webmin and Apache Parquet and learn effective mitigation strategies for enhanced cybersecurity.
5/5/2025

Explore recent UK retail cyberattacks, including Harrods' incident, and gain insights on enhancing cybersecurity resilience.
5/3/2025

Discover how to safeguard against WP-Antymalwary-bot malware with expert tips for WordPress security.
5/2/2025

Delve into APT28's tactics, campaigns, and implications for cybersecurity.
5/1/2025

Explore key security and usability challenges in Microsoft 365 to enhance organizational efficiency and protect data.
4/30/2025

Discover critical vulnerabilities in Commvault and Broadcom, plus essential mitigation strategies for CISOs to enhance security.
4/29/2025

Explore CVE-2025-31324, a critical SAP NetWeaver vulnerability with urgent remediation strategies for CISOs.
4/28/2025
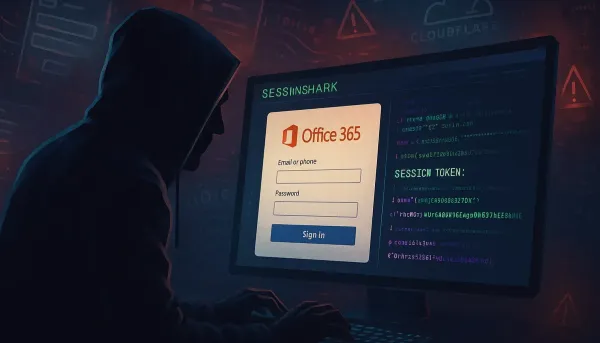
Discover how SessionShark phishing toolkit bypasses MFA, jeopardizing Office 365 security. Learn defenses against this threat.
4/26/2025
Explore the Blue Shield of California data breach, PHI exposure, and crucial recommendations for HIPAA compliance.
4/24/2025

Discover WhatsApp's Advanced Chat Privacy features enhancing data security and user control in digital communication.
4/24/2025

Explore privilege escalation vulnerabilities in Google Cloud Composer and Erlang/OTP, their impacts, and key mitigation strategies.
4/23/2025

Explore the evolution of Microsoft's security efforts and the Entra incident's implications for cybersecurity professionals.
4/22/2025

Explore the rise of OAuth phishing attacks targeting Google and effective mitigations for organizations.
4/21/2025

Explore SuperCard X malware, its NFC relay tactics, and strategies for CISO professionals to safeguard against evolving threats.
4/20/2025

Explore risks from the Oracle Cloud breach and get actionable security insights for your organization. Stay ahead of potential threats!
4/19/2025

Discover CVE-2025-32433, a severe RCE vulnerability in Erlang/OTP SSH, its impact, and essential mitigation strategies for security teams.
4/18/2025

Explore the implications of the CVE program funding crisis and its future. Key insights for sustainable vulnerability management.
4/17/2025
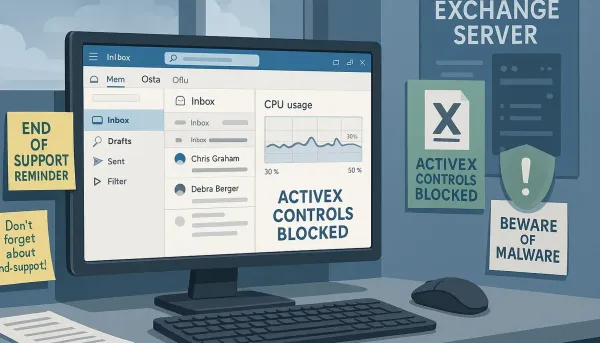
Explore critical changes in Outlook, ActiveX, and Exchange Server impacting enterprise security and operational practices for CISOs.
4/16/2025

Discover ResolverRAT, its tactics, impacts, and critical defenses for healthcare sectors.
4/15/2025
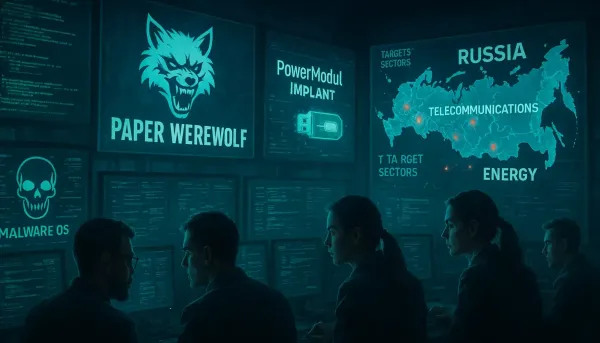
Explore the tactics and implications of Paper Werewolf's PowerModul implant targeting Russian sectors.
4/13/2025

Explore Operation Endgame's disruption of Smokeloader and its implications for cybersecurity.
4/12/2025

Explore recent security issues, licensing troubles, and outages in Microsoft services and learn how to navigate these challenges effectively.
4/11/2025

Discover key insights on the critical FortiSwitch vulnerability and effective mitigation strategies for organizations.
4/10/2025
Explore the alarming capabilities of Neptune RAT and strategies to secure your systems. Learn about this insidious malware now.
4/9/2025

Explore the implications of the Everest ransomware gang's leak site defacement and what it means for cybersecurity strategies.
4/8/2025
Explore Google's Sec-Gemini v1 AI model enhancing cybersecurity threat intelligence for CISO leaders.
4/7/2025

Explore the CVE-2025-22457 vulnerability in Ivanti Connect Secure. Learn mitigation strategies and threat exploitation tactics.
4/6/2025
Explore Fast Flux DNS's role in cyber threats and mitigation strategies for CISOs. Stay ahead in cybersecurity measures.
4/5/2025

North Korean IT workers pose a rising threat to European firms, adapting tactics and exploiting vulnerabilities. Learn how to defend.
4/3/2025

Discover how international efforts dismantled Kidflix, a dark web hub for child exploitation. Learn about cybersecurity implications.
4/3/2025

Unlock new insights on Google’s end-to-end encryption for Gmail and its impact on email security and privacy compliance.
4/2/2025
Discover the rising threat of malicious code in WordPress mu-plugins and how to protect your site effectively.
4/1/2025

Discover the evolution of FamousSparrow APT techniques and tactics targeting high-value sectors in cybersecurity. Learn key defenses!
3/28/2025

Explore the credential stuffing threat landscape and Atlantis AIO implications. Learn effective cyber defenses against attacks.
3/27/2025

Explore the implications of 23andMe's bankruptcy on genetic data privacy and security amid urgent consumer concerns.
3/26/2025

Explore the Arcane Stealer malware tactics, targets, and key mitigation strategies to protect sensitive information.
3/21/2025

Discover the urgent threats from unpatched Windows zero-day vulnerabilities and their global implications for cybersecurity.
3/20/2025
Explore Google's strategic $32 billion acquisition of Wiz to enhance cloud security offerings and multi-cloud protection.
3/19/2025

Explore the supply chain attack on tj-actions and learn how to secure your CI/CD pipelines effectively.
3/18/2025

Explore critical vulnerabilities in Adobe Acrobat and learn effective mitigation strategies for secure document handling.
3/17/2025

Explore the evolution of LockBit ransomware and its impact, focusing on Rostislav Panev's extradition and emerging threats.
3/15/2025

Uncover the ClickFix phishing campaign's tactics, impact, and how to protect your organization in an evolving cybersecurity landscape.
3/14/2025

Explore key insights on critical technology vulnerabilities and effective mitigation strategies for organizations today.
3/13/2025

Discover the latest high-risk vulnerabilities in Chrome's 2025 updates and effective strategies for cybersecurity defense.
3/11/2025

Explore insider sabotage and external exploitation techniques in cybersecurity cases. Learn to safeguard against these threats.
3/10/2025

Explore the Garantex cryptocurrency case and its implications for regulation, law enforcement, and financial crime combatting efforts.
3/9/2025

Discover how Silk Typhoon's tactics target cloud services and IT supply chains, and learn crucial defense strategies for organizations.
3/7/2025

Meta's proactive measures against scams like 'pig butchering' reveal the urgent need for cybersecurity collaboration.
11/25/2024

Explore the emergence of Gelsemium's Linux malware, WolfsBane and Firewood, and its implications for cybersecurity.
11/23/2024

Explore the tactics of the Scattered Spider cybercrime gang and their implications for cybersecurity resilience.
11/22/2024

A deep dive into the ESET phishing attack and key recommendations for CISOs to enhance organizational security.
10/20/2024

Explore how EDRSilencer jeopardizes EDR systems and learn countermeasures to enhance cybersecurity.
10/17/2024

Explore the implications of Sipulitie and Tsätti takedowns in dark web crime. Key insights for CISOs in combating organized cybercrime.
10/16/2024

Explore the evolving TrickMo banking Trojan, its tactics, and defense strategies for Android security.
10/15/2024

Explore APT34's exploitation techniques and CVE-2024-30088 vulnerabilities.
10/14/2024

Uncover the critical Veeam CVE-2024-40711 exploit and ransomware impacts. Immediate security measures necessary for CISO preparedness.
10/12/2024

Discover critical vulnerabilities in Mozilla and GitLab. Ensure your organization is protected with effective strategies and updates.
10/11/2024

Uncover GoldenJackal's tactics against air-gapped systems and enhance your cybersecurity defenses.
10/10/2024

Explore the Salt Typhoon breach, its implications for telecom security and national interests, and defense strategies for organizations.
10/9/2024

Explore the American Water Works cyber attack and strategies to enhance utility cybersecurity resilience.
10/8/2024

Explore recent CUPS vulnerabilities exposing critical risks in print services and crucial mitigation strategies for CISOs.
10/4/2024

Explore Kia's cybersecurity vulnerabilities and their implications for the automotive industry in this timely blog post.
10/1/2024

Explore Octo2, the latest banking trojan, and its implications for mobile banking security. Stay informed, stay secure!
9/27/2024

Learn about CVE-2024-7593, its exploitation risks, and how to mitigate the threats effectively.
9/26/2024

Explore Telegram's policy change on user data sharing and its implications for privacy in the landscape of cybersecurity.
9/25/2024

Explore critical vulnerabilities in Cisco's Smart Licensing and ISE, and learn essential mitigation strategies for cybersecurity.
9/5/2024

Discover how APT-C-60 exploits zero-day vulnerabilities in WPS Office and the implications for cybersecurity.
8/29/2024

Explore BlackByte ransomware's tactics exploiting VMware ESXi vulnerabilities and learn vital security measures for enterprises.
8/29/2024

Explore how Iranian hacking group Pioneer Kitten collaborates with ransomware gangs, exploiting vulnerabilities across critical sectors.
8/29/2024

Discover the ASCII smuggling threat in Microsoft 365 Copilot and learn effective mitigation strategies for CISOs.
8/28/2024

Explore Uber's $324 million GDPR fine and learn key compliance strategies for data protection in a dynamic regulatory landscape.
8/28/2024

Explore how Volt Typhoon exploits CVE-2024-39717 and critical steps for CISOs to enhance their cybersecurity defenses.
8/28/2024

Explore the critical access control flaw in SonicWall's SonicOS and necessary mitigation strategies for CISOs and teams.
8/27/2024

Explore insights from the Halliburton cyberattack and its implications for critical infrastructure cybersecurity measures.
8/25/2024

Dive into CVE-2024-7971's impact on Chrome security and critical mitigation strategies for organizations.
8/22/2024
Explore new phishing strategies targeting banks in Central Europe and how to mitigate these threats effectively.
8/21/2024

Explore a detailed analysis of a cloud extortion campaign exploiting .env files, revealing key security flaws for CISOs.
8/20/2024

Discover the ArtiPACKED vulnerability in GitHub Actions artifacts, a new attack vector posing severe risks to CI/CD workflows and cloud environments.
8/15/2024

Explore CVE-2024-7589, a severe vulnerability in FreeBSD's OpenSSH, and learn how to protect systems from unauthenticated RCE risks.
8/13/2024

Explore the QuickShell RCE attack on Google’s Quick Share, highlighting vulnerabilities, exploitation methods, and proactive security measures for CISOs.
8/12/2024

Explore CVE-2024-38200, a severe Microsoft Office vulnerability, and learn essential mitigation strategies to protect your organization.
8/10/2024

Explore the 0.0.0.0 Day vulnerability affecting major web browsers like Chrome, Firefox, and Safari, and learn how it threatens cybersecurity.
8/9/2024

Explore the advanced threat posed by BlackSuit ransomware, its tactics, and how organizations can defend against this sophisticated evolution of Royal ransomware.
8/8/2024
Discover how SLUBStick transforms kernel vulnerabilities into critical threats, bypassing advanced defenses and affecting Linux systems worldwide.
8/7/2024

Discover how Evasive Panda, a China-linked group, uses DNS poisoning to conduct cyber espionage in 2023, targeting insecure software updates.
8/6/2024

Discover how AI exploits HDMI EM emissions for cyber espionage, revealing new vulnerabilities in digital systems. Essential insights for CISOs.
8/5/2024

Explore APT41's sophisticated breach of a Taiwanese institute, analyzing their advanced techniques, tools like ShadowPad and Cobalt Strike, and defensive strategies.
8/4/2024

Discover how SideWinder's latest cyber campaign targets maritime facilities using spear-phishing and DLL side-loading, compromising security in key regions.
7/31/2024

Learn how OAuth and XSS flaws in popular services can lead to account takeovers and data breaches, affecting millions of users worldwide.
7/29/2024

Millions of Intel and ARM devices are at risk due to the 'PKFail' Secure Boot bypass. Understand its impact and learn critical mitigation steps.
7/28/2024

Gemini reveals a data breach through a third-party banking partner, potentially compromising sensitive customer information. Protect your assets now.
7/27/2024

A North Korean hacker deceived a US cybersecurity firm with AI-generated images and a stolen ID, prompting an FBI investigation into the breach.
7/26/2024

Infoblox exposes a Chinese cybercrime network linked to European football, gambling, and trafficking. Uncover the detailed findings and implications.
7/22/2024

Hackers breach Disney, leaking internal communications and affecting key projects. Explore the full scope of the data breach and its security impact.
7/21/2024
A CrowdStrike update led to a major Microsoft outage, spotlighting the need for effective update management. Learn how to avoid similar issues.
7/21/2024
2024's top cyber threats include APTs, ransomware, zero-days, supply chain attacks, and more. Stay ahead with key insights and protection strategies.
7/18/2024