
Evasive Panda Threat - DNS Poisoning Cyber Espionage
In mid-2023, the cybersecurity landscape witnessed a stark reminder of the evolving sophistication in cyber espionage techniques. The China-linked threat actor known as Evasive Panda, also tracked as StormBamboo, Daggerfly, and StormCloud, executed a highly targeted and sophisticated attack leveraging DNS poisoning at the ISP level. This attack, aimed at distributing malware through compromised software update mechanisms, highlights the growing threat posed by nation-state actors in cyberspace. As cybersecurity professionals, understanding the intricacies of this attack is crucial to fortifying defenses against similar future threats.
The Evasive Panda Threat Group: An Overview
Evasive Panda, active since at least 2012, has established itself as a formidable player in the realm of cyber espionage. Known for deploying a variety of malware across different platforms, including macOS, Windows, and network appliances, the group’s operations reflect a high degree of skill and adaptability. Their arsenal includes backdoors like MgBot (also known as POCOSTICK) and Nightdoor, which have been used to harvest sensitive information from targeted entities.
More recently, Evasive Panda has been associated with the use of a macOS malware strain called MACMA, first observed in 2021. This group’s recent activities have further expanded its notoriety, particularly through the sophisticated attack vector involving ISP-level DNS poisoning, which we’ll delve into.
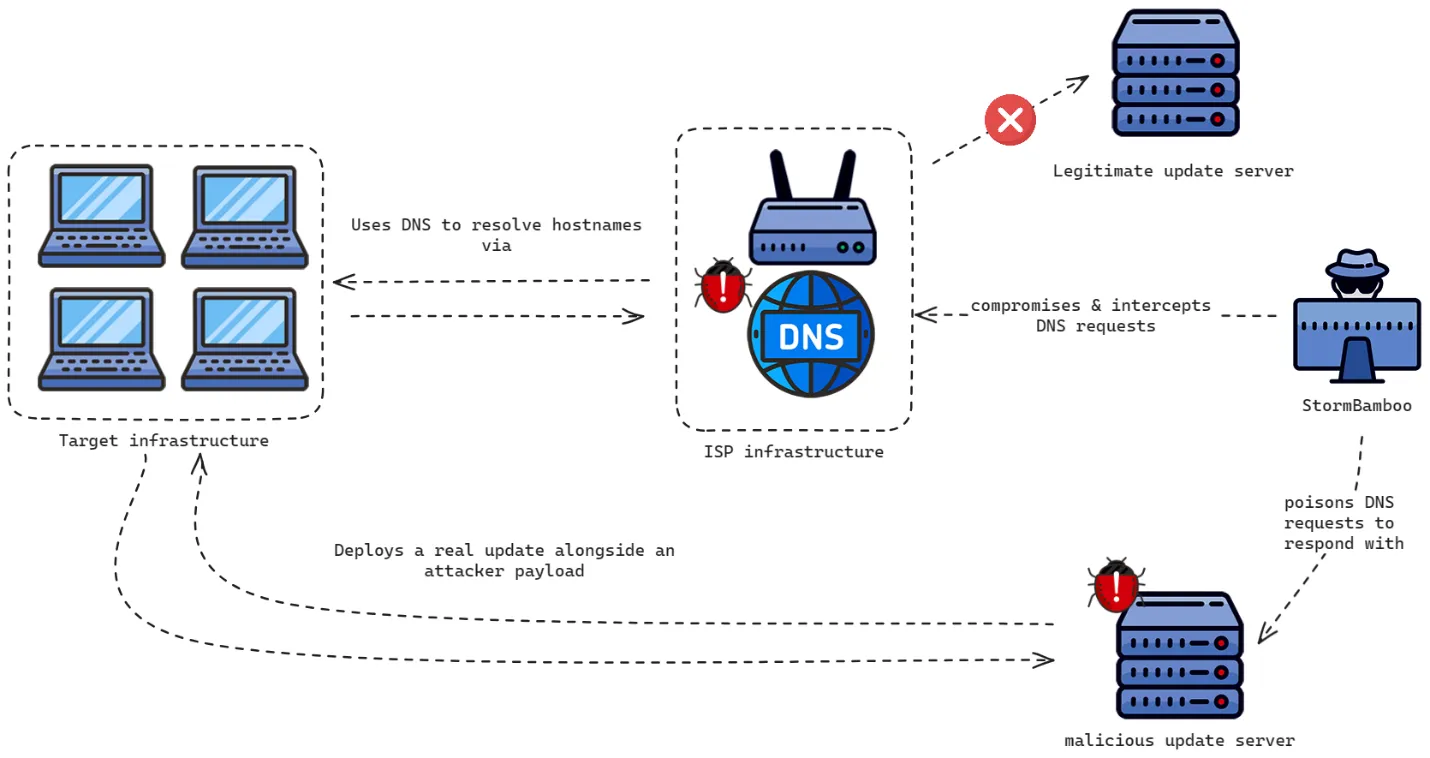
The Attack Vector: DNS Poisoning at the ISP Level
Exploiting Insecure Software Update Mechanisms
The core of Evasive Panda’s attack strategy in 2023 revolved around compromising an unnamed ISP to manipulate DNS responses for specific domains. This manipulation targeted software applications that used insecure update mechanisms, particularly those relying on HTTP rather than HTTPS, and did not validate digital signatures adequately. By altering DNS query responses, the threat actor redirected legitimate software update requests to malicious servers under their control, effectively distributing malware instead of the intended updates.
Case Study: 5KPlayer and youtube-dl
One notable instance involved the multimedia application 5KPlayer, which checks for updates to the open-source YouTube video downloader, youtube-dl. Evasive Panda exploited this process by using DNS poisoning to serve a backdoored installer from their command-and-control (C2) server. This installer included the MACMA backdoor, enabling the group to establish persistent access to the compromised systems.
The Role of ISP-Level Compromise
The sophistication of this attack lies in its execution at the ISP level. By compromising the ISP’s infrastructure, Evasive Panda was able to poison DNS responses upstream, affecting multiple organizations simultaneously. The attack was particularly challenging to detect because it circumvented traditional perimeter defenses, exploiting the trust placed in ISPs as legitimate traffic routers.
Malware Arsenal: MgBot, MACMA, and Beyond
MgBot (POCOSTICK)
MgBot, a modular malware framework, has been a staple in Evasive Panda’s toolkit for years. It supports various plugins that enable network scanning, browser data exfiltration, keylogging, and password dumping. This flexibility makes MgBot a versatile tool for prolonged espionage campaigns, particularly against high-value targets.
MACMA Backdoor
The MACMA backdoor, first identified by Google in 2021, represents a significant evolution in Evasive Panda’s macOS-targeting capabilities. MACMA is a feature-rich backdoor capable of device fingerprinting, command execution, screen capture, keylogging, and audio recording. Its deployment through DNS poisoning underscores the threat actor’s ability to adapt and weaponize new attack vectors effectively.
Chrome Extension: RELOADEXT
In a post-compromise phase, Evasive Panda deployed a malicious Google Chrome extension named RELOADEXT. This extension, installed via a custom binary, was designed to exfiltrate browser cookies and email data to a Google Drive account controlled by the attackers. This tactic highlights the group’s multifaceted approach to data collection, leveraging both traditional malware and innovative browser-based techniques.
Analysis and Insights
The Growing Threat of DNS Poisoning
The attack executed by Evasive Panda illustrates a broader trend in cyber espionage: the increasing use of DNS poisoning as a tool for sophisticated, hard-to-detect attacks. By compromising ISPs, threat actors can effectively bypass conventional security measures, delivering malicious payloads through trusted channels. This method also demonstrates the vulnerabilities inherent in relying on insecure update mechanisms, particularly those that do not enforce HTTPS or validate digital signatures.
Defensive Strategies
To defend against such attacks, organizations must prioritize the following:
- Enforce HTTPS: Ensure that all software update mechanisms utilize HTTPS with strict certificate validation to prevent man-in-the-middle attacks.
- Digital Signature Validation: Implement robust validation of digital signatures for all software updates to ensure the integrity and authenticity of the code.
- DNS Security Measures: Consider deploying DNS Security Extensions (DNSSEC) and monitoring DNS traffic for anomalies that could indicate poisoning attempts.
- ISP Collaboration: Establish strong partnerships with ISPs to ensure rapid response and mitigation strategies in the event of infrastructure compromise.
The Need for Continuous Vigilance
The Evasive Panda incident underscores the importance of continuous vigilance in cybersecurity. Threat actors are constantly evolving their tactics, and the ability to detect and respond to such sophisticated attacks requires a proactive and well-coordinated approach. Organizations must invest in advanced threat detection and response capabilities, as well as in fostering a culture of security awareness that extends beyond traditional IT boundaries.
Conclusion
The 2023 DNS poisoning attack by Evasive Panda is a sobering reminder of the lengths to which nation-state actors will go to achieve their objectives. By compromising an ISP and exploiting insecure software update mechanisms, this threat actor demonstrated a new level of sophistication in cyber espionage. As the cybersecurity landscape continues to evolve, it is imperative that organizations adopt a proactive and multi-layered defense strategy to protect against such advanced threats. The lessons learned from this incident should inform future security practices, ensuring that the risks posed by DNS poisoning and similar attack vectors are adequately mitigated.
The evolving tactics of groups like Evasive Panda demand not only technical countermeasures but also a strategic shift in how we approach cybersecurity at the organizational and national levels. As we move forward, the integration of advanced threat intelligence, continuous monitoring, and strong ISP collaboration will be critical in safeguarding against the ever-present threat of cyber espionage.