SLUBStick Exploit - 99% Success in Kernel Attacks
In the relentless arms race between cybersecurity defenders and attackers, new vulnerabilities emerge as both sides innovate and adapt. The recent discovery of SLUBStick, a novel exploitation technique targeting the Linux kernel, has sent shockwaves through the cybersecurity community. Developed by researchers at Graz University of Technology, SLUBStick has demonstrated a staggering 99% success rate in converting limited heap vulnerabilities into full-fledged arbitrary memory read-and-write capabilities. This blog post delves into the intricacies of SLUBStick, exploring its operation, implications, and the critical measures needed to mitigate this emerging threat.
The Rise of SLUBStick: A New Exploitation Paradigm
Background and Context
The Linux kernel, the backbone of countless systems worldwide, has always been a prime target for attackers due to its widespread use and critical role in system operations. Over the years, numerous vulnerabilities have been discovered and patched, but the kernel’s complexity ensures that new attack vectors continually emerge. SLUBStick represents a significant advancement in the exploitation of kernel heap vulnerabilities, specifically targeting the SLUB memory allocator—a component responsible for efficient memory management within the kernel.
From Low-Impact Bugs to System Compromise
Historically, cross-cache attacks—techniques that exploit memory reuse in the kernel’s allocator—have been considered unreliable. With a success rate hovering around 40%, these attacks were often dismissed due to their propensity to crash the system rather than achieve their intended malicious outcomes. SLUBStick changes this calculus dramatically. By exploiting a timing side-channel vulnerability within the allocator, SLUBStick achieves a cross-cache attack with a success rate exceeding 99%. This leap in reliability elevates seemingly minor heap vulnerabilities into significant threats, capable of bypassing even the most advanced kernel defenses.
Technical Deep Dive: How SLUBStick Works
The Anatomy of a SLUBStick Attack
SLUBStick operates in several stages, each meticulously designed to exploit weaknesses in the Linux kernel’s memory management. The attack begins by identifying a heap vulnerability, such as a double-free, use-after-free, or out-of-bounds write. These vulnerabilities, while often limited in scope, serve as the entry point for SLUBStick’s more sophisticated exploits.
Stage 1: Exploiting the Timing Side-Channel
The first stage of SLUBStick involves leveraging a timing side-channel attack on the SLUB allocator. By carefully measuring the time it takes for memory allocation and deallocation, the attacker can infer critical information about the kernel’s memory reuse patterns. This timing data is crucial for reliably triggering the allocator to recycle specific memory chunks—an essential step in ensuring the success of the subsequent cross-cache attack.
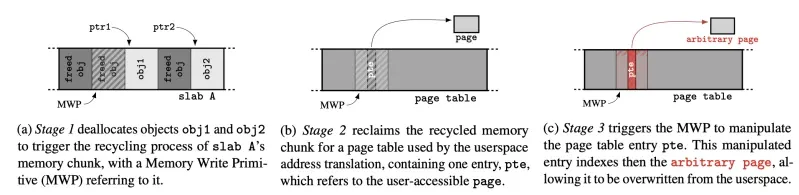
Stage 2: Memory Recycling and Page Table Manipulation
Once the attacker has gathered sufficient timing data, SLUBStick moves to the second stage: triggering the recycling of memory pages. This is achieved by first freeing a targeted memory chunk and then allocating new objects to reclaim the same slab page. By controlling this process, the attacker can repurpose the memory chunk for critical data structures, such as page tables.
With the memory chunk now holding sensitive kernel data, SLUBStick leverages the initial heap vulnerability to overwrite page table entries. This manipulation grants the attacker arbitrary read-and-write access to system memory, effectively allowing them to bypass kernel defenses and escalate privileges.
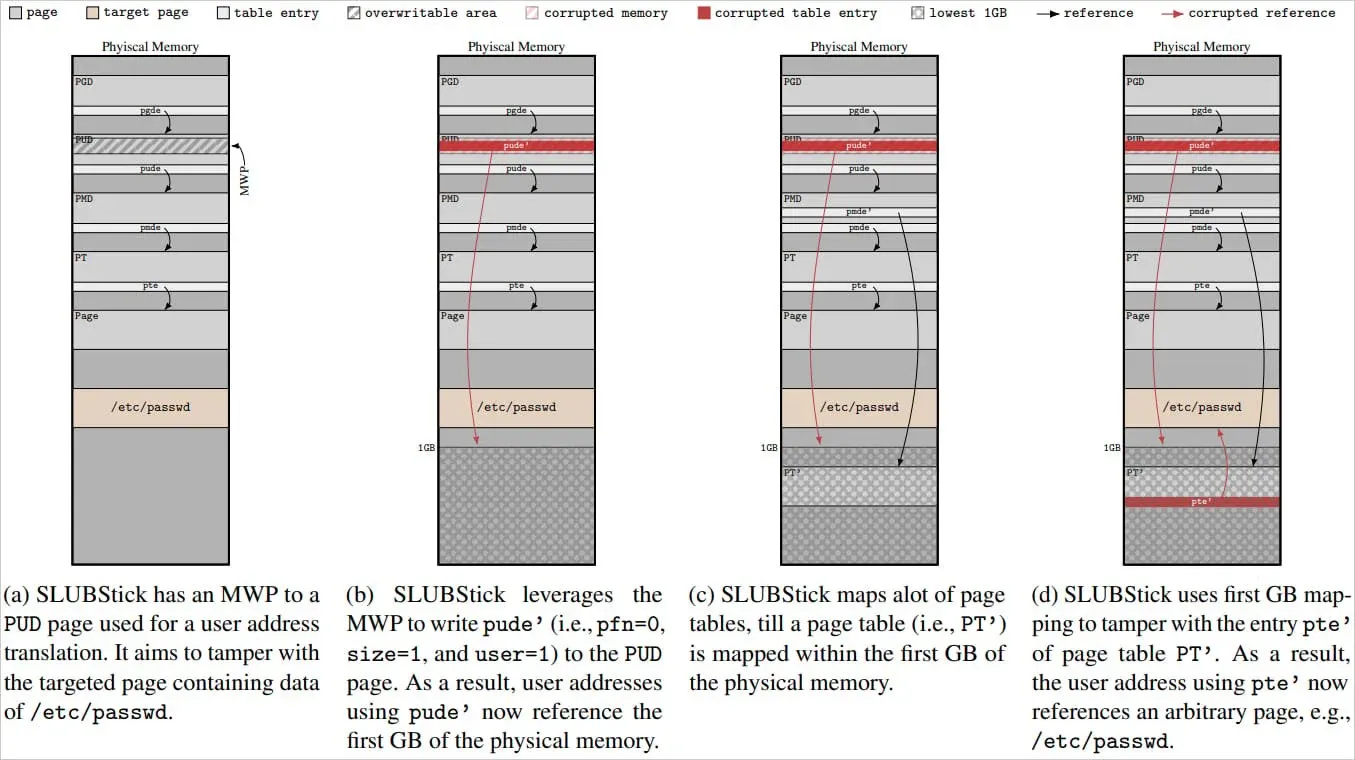
Stage 3: Achieving Arbitrary Memory Access
In the final stage, the attacker uses their newly acquired memory write primitive (MWP) to modify critical kernel structures. For example, by altering page frame numbers and access permissions, the attacker can gain unauthorized access to any physical memory page. This capability can be used to modify kernel code, tamper with sensitive files such as /etc/passwd, or even maintain persistent control over the compromised system.
Implications and Real-World Impact
SLUBStick’s Broader Threat Landscape
The implications of SLUBStick extend far beyond the immediate threat of privilege escalation and container escapes. By transforming limited heap vulnerabilities into full memory manipulation capabilities, SLUBStick amplifies the effectiveness of existing exploit techniques. One notable example is its potential to enhance the success rate of the DirtyCred exploit, which relies on similar principles of memory reuse and manipulation.
Moreover, SLUBStick’s effectiveness against a wide range of Linux kernel versions, including 5.19 and 6.2, underscores its versatility. These versions, while no longer supported, remain in use across many systems, particularly in environments where updates are infrequent or impractical. As a result, systems running these kernels are particularly vulnerable to exploitation.
Bypassing Advanced Kernel Defenses
One of the most concerning aspects of SLUBStick is its ability to bypass modern kernel defenses, including Supervisor Mode Execution Prevention (SMEP), Supervisor Mode Access Prevention (SMAP), and Kernel Address Space Layout Randomization (KASLR). These defenses, designed to protect the kernel from unauthorized memory access and control-flow integrity violations, are rendered ineffective by SLUBStick’s advanced manipulation techniques.
Mitigation Strategies and Recommendations
Immediate Actions for Security Teams
Given the severity of the SLUBStick vulnerability, immediate action is required to mitigate the risk of exploitation. Security teams should prioritize the following measures:
-
Patch Vulnerable Systems: Ensure that all systems running Linux kernel versions 5.19, 6.2, or any other affected versions are updated to the latest supported releases. This is the most effective way to protect against SLUBStick and other related vulnerabilities.
-
Enhance Monitoring and Detection: Implement advanced monitoring tools capable of detecting unusual memory allocation patterns and potential timing side-channel attacks. Early detection is key to preventing successful exploitation.
-
Employ Kernel Hardening Techniques: Consider implementing additional kernel hardening measures, such as randomizing allocator caches and reinforcing page table access controls. While these may not provide complete protection, they can reduce the likelihood of successful exploitation.
-
Strengthen Container Security: For environments that rely heavily on containerization, it’s crucial to adhere to best practices for container security. This includes applying the principle of least privilege, regularly scanning for vulnerabilities, and ensuring proper isolation between containers and the host system.
Long-Term Considerations
In addition to immediate mitigations, organizations should consider longer-term strategies to enhance kernel security:
-
Invest in Research and Development: As SLUBStick demonstrates, attackers are continually developing new techniques to exploit kernel vulnerabilities. Organizations should invest in research and development to stay ahead of these evolving threats.
-
Adopt Comprehensive Security Frameworks: Implementing security frameworks like SELinux or AppArmor can provide additional layers of defense, making it more difficult for attackers to exploit kernel vulnerabilities.
-
Promote Security Awareness: Educating staff about the latest threats and best practices is essential for maintaining a robust security posture. Regular training and awareness programs can help prevent security lapses that could lead to exploitation.
Conclusion
SLUBStick represents a significant advancement in kernel exploitation techniques, posing a serious threat to Linux systems worldwide. By converting limited heap vulnerabilities into powerful memory manipulation capabilities, SLUBStick bypasses modern kernel defenses and enables attackers to gain full control over targeted systems.
The discovery of SLUBStick serves as a stark reminder of the ongoing challenges in securing complex operating systems against sophisticated attacks. As the cybersecurity landscape continues to evolve, organizations must remain vigilant, proactive, and committed to continuously improving their security measures. By taking immediate action to patch vulnerable systems, enhance monitoring, and invest in long-term security strategies, organizations can better protect themselves against this and future threats.
References:
- Graz University of Technology. “SLUBStick: Reliable Cross-Cache Attacks in the Linux Kernel.” Usenix Security Symposium, 2024.